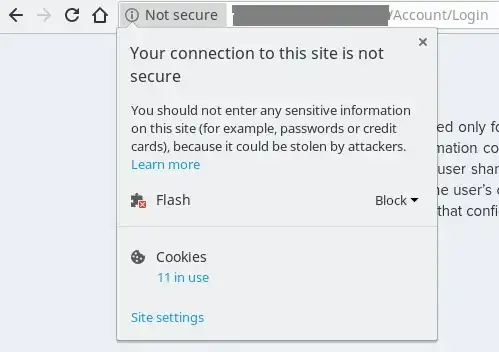
I work for a corporation and we are all given a kind of employee login system whose URL goes like this in the image below. (Sorry, I cannot disclose the full URL.)
I thought "Not Secure" had something to do with SSL certificates or something like that, but after clicking "view site information", I got this:
I manually blocked Flash, but don't know what possibly can be done with cookies and also if possible I couldn't take a risk for doing that on a corporate website.
I have a few questions in mind:
What exactly does "Not Secure" mean? Does it mean it's a "HTTP only" website?
What are all the possible reasons for a site to be "Not Secure"?
Is it OK to have an account login site that is "Not Secure"?
Do cookies have something to do with a site being not secure?
What are possible ways to make this site secure and how can I inform those responsible to make it secure?