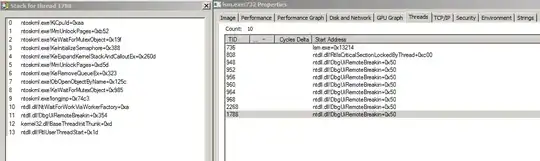
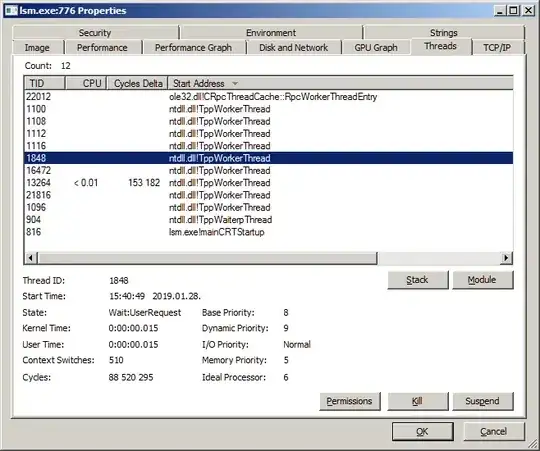
Ignore the down votes. If it is not a "TppWorkerThread" it could be mimikats malware... you can mitigate against mimikats & other debugger attacks by disabling debugging as described here: https://medium.com/blue-team/preventing-mimikatz-attacks-ed283e7ebdd5
If you are missing the necessary group policies to disable debugging (as was I), follow the simple steps here (This is relevant to windows 7.)
And for your convenience, so you don't have to install security compliance manager & SQL server express, you can just use this LocalGPO.msi
- Run and install the file “LocalGPO.msi” on the workstation/server
- Open command prompt and browse to : “C:\Program Files (x86)\LocalGPO”
- Run following command “Cscript LocalGPO.wsf /ConfigSCE"
- Now MSS Settings (and others) will be visible in Security Options in Local Group policy settings.
How to prevent this? Further Prevention: Keep on hardening your system and environment, including your router firmware & hardware... keep everything up-to-date... there are a million different ways for mimikats infections, probably the most common debugger type attack out there.
This video is incredibly informative and is relevant to understand common methods a debugger attack could happen. In other words, keep your windows machine up-to-date & bear in mind mimikats is just one of hundreds of exploitation scripts in metasploit.
Run SFC /Scannow, and DISM at commandline to check for system corruption:
Dism /Online /Cleanup-Image /ScanHealth
If corruption detected, run:
Dism /Online /Cleanup-Image /RestoreHealth
As a last but often necessary resort for bad malware infections, you may want to consider doing an in-place dist-upgrade to clean up any hidden malware or changes that may have been done to the system and its permissions. Once a machine has been hit the damages may be irreparable without this. This is what I had to do to fix this exact same debugger problem.
Further Prevention: Just as one hardware example, if you are running an AMD Ryzen processor debugger exploits may be be taking place as an adjunct to hardware/chipset level exploits... be sure your motherboard firmware is up-to-date. Asus has told me personally, 2-3 weeks before the time of this post, they are still working on patching the following network/remotely exploitable hardware vulnerabilities threats:
- CVE-2018-8930: The AMD EPYC Server, Ryzen, Ryzen Pro, and Ryzen Mobile processor chips have insufficient enforcement of Hardware Validated Boot, aka MASTERKEY-1, MASTERKEY-2, and MASTERKEY-3.
- CVE-2018-8931: The AMD Ryzen, Ryzen Pro, and Ryzen Mobile processor chips have insufficient access control for the Secure Processor, aka RYZENFALL-1.
- CVE-2018-8932: The AMD Ryzen and Ryzen Pro processor chips have insufficient access control for the Secure Processor, aka RYZENFALL-2, RYZENFALL-3, and RYZENFALL-4.
- CVE-2018-8933: The AMD EPYC Server processor chips have insufficient access control for protected memory regions, aka FALLOUT-1, FALLOUT-2, and FALLOUT-3.
- CVE-2018-8934: The Promontory chipset, as used in AMD Ryzen and Ryzen Pro platforms, has a backdoor in firmware, aka CHIMERA-FW.
- CVE-2018-8935: The Promontory chipset, as used in AMD Ryzen and Ryzen Pro platforms, has a backdoor in the ASIC, aka CHIMERA-HW.
- CVE-2018-8936: The AMD EPYC Server, Ryzen, Ryzen Pro, and Ryzen Mobile processor chips allow Platform Security Processor (PSP) privilege escalation.