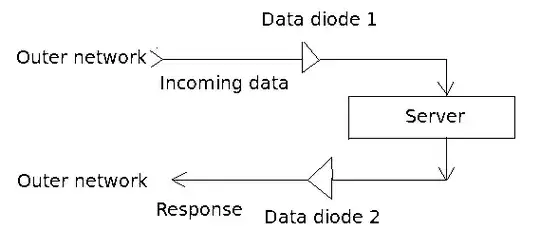
I have a software which processes pure numerical data and gives some response.
To make it safe, I put it behind two data diodes: one for incoming data, and one for outcoming response. The data diodes are implemented as customer-specific hardware.
Important point: the data diodes are 4-bit wide and thus allow only 4-bit words. The data is purely numerical and encoded like this in binary form:
0000 = '0'
0001 = '1'
0010 = '2'
0011 = '3'
0100 = '4'
0101 = '5'
0110 = '6'
0111 = '7'
1000 = '8'
1001 = '9'
1010 = '.'
1011 = ';' (separator)
Is my software behind the data diodes is still safe from the hacker attacks?
I believe yes, because the 4-bit data words do not allow hacker send any malicious commands. If they were 8-bit wide, then all ASCII characters would come through and the software would be vulnerable.