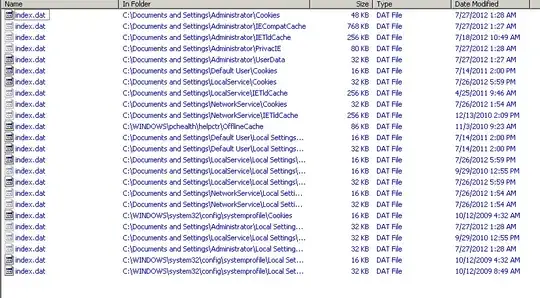
I have a system that contains highly sensitive data that does not reside on the Internet. However, when I was going through the machine recently, I detected that it had cookies, and temporary internet files stored on it. While I can find the date these were created, I need to be able to obtain the date of last Internet access in a verifiable manner. The machine is Windows XP, and I have full administrative access. I have already looked in the Event Viewer, there was no information there, as such. The last modification date for the Temporary Internet Files folder is a few years ago, so that has not served as an indication either. Is there some resource, or some logs, that Windows has that can tell me when the last connection happened, and if possible, how?
Note: This is not within a corporate network, or any similar internal network.