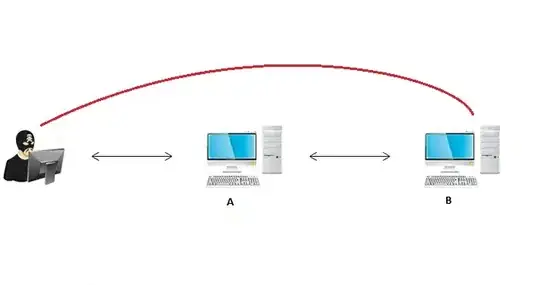
I am trying to execute a ping throught proxychains, after create SSH tunnel, but the response of the petition is Destination Host Unreachable.
Concretly, I want to do a lab about pivoting. The attacker machine have visibility over A machine, but not over B machine. A machine have visibility over B machine. In this probe, I want to verify created tunnel execute a ping to B machine from attacker machine.
I have this on /etc/proxychains.conf :
socks4 127.0.0.1 9050
And I used these two commands:
ssh -D 9050 user@192.168.1.132
ssh -f -N -D 9050 user@192.168.1.132
But any of them allow me to execute a ping with proxychains.
What can I do?