Recently, I've worked on setting certificate pinning for our mobile app. I'm using the hash of the Subject Public Key Information (SPKI) for the pinning. Now, I was under the impression that SPKI will be the same if I'll create another certificate from the same private key. So I tried it out - I created a private key using SSL and a matching CSR. Now, I signed this CSR twice using different private keys, and to my surprise - the SPKI (and the pin hash) was not the same. Is that the expected behavior? Or is it something I'm missing? Is the PKI in the certificate also signed?
Those are the openssl command I've used:
To generate a CSR:
openssl req -new -sha256 -key private.key -out private.csr
To generate CA private key:
openssl genrsa -des3 -out ca.key 2048
To sign the CSR:
openssl x509 -req -days 365 -in private.csr -signkey ca.key -out test.crt
This is the beginning of the SPKI from the first certificate:
BA 86 D3 0E E8 CC F3 C0 A2 B9 1E 8B BA 45 80 11 EF 13 CB 4F 76 CE A8 6A
And this is the beginning of the SPKI from the second certificate:
CC 96 B3 AB EA 0D FC 66 91 D8 E2 50 2B A7 8F 63 91 4C 7E 10 A3 48 1E 9F
To compute the hashes, I used the simplest way - imported the certificates to the mac keychain, and open them:
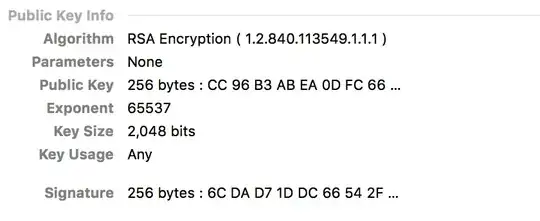
I also used this python script from TrustKit to get the certificate pinning hash, and it also was different.