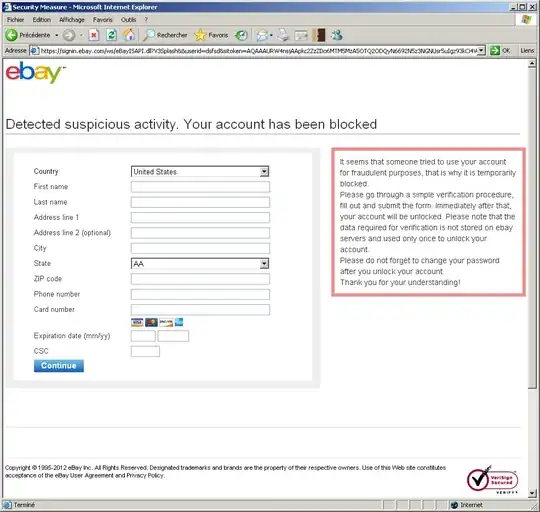
I've heard many times that malware like Zeus, SpyEye and Citadel are able to do browser injections to steal credit card data. How do they do it? how do browser "injections" work? How are they able to tamper all browser data? Furthermore, why don't browser extension writers use something like browser injections to ensure compatibility with all browsers?
Additional question: Is there any source code you could look at as an example? You could make so much slick stuff with it!