I have a question about Remote Attestation and measured boot with a TPM-Module.
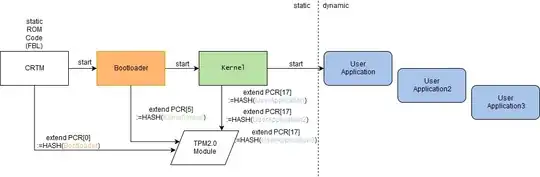
The illustration shows my project schematically. A TPM module will be used to measure the boot process and validate user applications. The kernel generates a hash value from all user applications and extends the PCR register 17. Authentication should be performed using the Remote Attestation Protocol. (Simplified:) For this the verifier sends the prover the challenge c (which includes a nonce, and information about which register he is interested in). The prover response with a signed (with an AIK Key because the EK Keys should not be used) messages of the PCR-Values (in this example PCR[17]). With the signature, the challenge knows that the response come from a TPM.
So far so good, but how does the verifier know that the PCR values are "correct"? Where do the reference values come from for comparison? Is there a local copy of the expected PCR values on the verifier's page? can you simply calculate them? (For example, the verifier knows the hash values of the user application and calculates the PCR values itself).
I am looking forward to more information and useful links. Thank you for your answers and help.