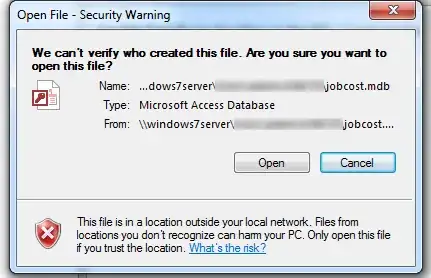
This error dialog is there to make users aware of the potentially dangerous source from where the file comes.
When you say
[B]ut currently, a user would just click run or open in the dialog box and the files in question would run or open.
this defies the reason for that warning to appear, so adding this as a trusted source is not decreasing security if what you say is true for all users.
Nonetheless, there are some assumptions that come with your setup:
- all people with access are trustworthy and
- the fileserver is sufficiently secured
If a rogue employee drops malicious code, no one gets a warning beforehand, so users might be inclined to execute macros, for example.
If an external attacker gains access to this file server (for example pivoting from an compromised endpoint), this would defy network segregation if the fileserver serves multiple segments (for example because it is the share for exchange between divisions).
Additionally, there might be implications for the endpoint security solution you are using - a trusted source might not be scanned. This depends on the actual product and settings, though.
You might also want to consider not having the share active all the time to contain ransomware damages to the local, infected, endpoint - even with a good backup strategy, there is cost to restoring from a backup.