I have a pcap file that contains 3 packets. I need to find a WEP key inside these packets. These packets contains only two IV. It's not a live attack so I can't try brute force.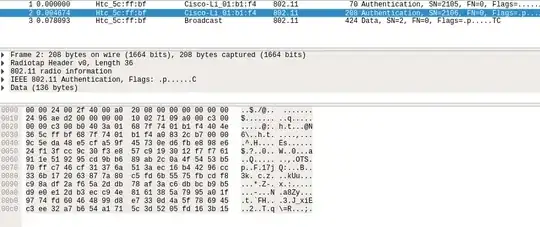
Asked
Active
Viewed 1.0k times
2
-
1Are the two IVs the same? If yes, got everything you need for an attack. – Tobi Nary Nov 04 '17 at 12:47
-
1Also, what does brute force have to do with it being a live attack? No one would do a brute force on any WiFi authentication live. Get a handshake, crack the password offline. – Tobi Nary Nov 04 '17 at 12:48
-
@SmokeDispenser they have different IVs. You are right it doesn't have anything to do with a live attack, thx. – Nov 04 '17 at 20:00
1 Answers
1
In order to break WEP you need to catch 2 packets with the same key and reused IVs. The number of packets in order to break the key depends on the length of the IV, but you usually need more than one thousand.
In your case probably your 3 packets do not share the same IVs. This means that you cannot break easily the key. Your only way will be brute forcing the key and for that, you do not need any live attack.
You can use airdecap-ng for bruteforce the key.
CarlosLannister
- 56
- 1