This security article from Apple says that 11.1 fixes the KRACK vulnerability for iPhone 7 and newer devices. But what about the older devices? Has Apple not fixed them or does the vulnerability not affect these devices?
1 Answers
It seems, that you were spot on with your questions. Several news sites report the same, for instance ArsTechnica mentions:
Update: As Ars readers have pointed out, Apple's support documentation states that the iOS KRACK fix is available for iPhone 7 and later, and for the early 2016, 9.7-inch iPad Pro and later. It is unclear whether this means previous devices are still vulnerable, or they had previously not been vulnerable and thus didn't need an update. Ars has reached out to Apple for comment.
EDIT:
I dug through the comments on ArsTechnica and found this post. It states the following:
For iOS, the bug was fixed in iOS 10.3.3. I was able to establish a theory based on firmware analysis and tested the theory on a few devices running older and newer iOS firmware. The pattern was that devices with A8 processors were vulnerable (crashed the Wi-Fi chip) if running iOS 10.3.2 or earlier, but models with older processors were not vulnerable for any iOS version I could test. (I wasn't able to test any A9 or newer models running iOS 10.3.2 or earlier, but firmware analysis points to them being vulnerable as there were fixes in 10.3.3.)
In the macrumors forum I've found this post, which says something else, I wasn't able to find the part in the transcripts until now. Maybe someone else can shed some light on this.
Yep apparently in the older devices iOS WPA2 implementation was not correctly done and as a side benefit are not vulnerable to KRACK. According to Steve Gibson of Security Now, iOS was not vulnerable to KRACK because they misimplemented the WPA2 specification. My guess is iP7 and up is when WPA2 was fixed and therefore now those devices need the patch! Perhaps Apple will relay this information soon to clear it up for all. That could mean the non iOS11 compatible devices are all fine as well.
So that might be the reason why there was only a fix for the newer devices.
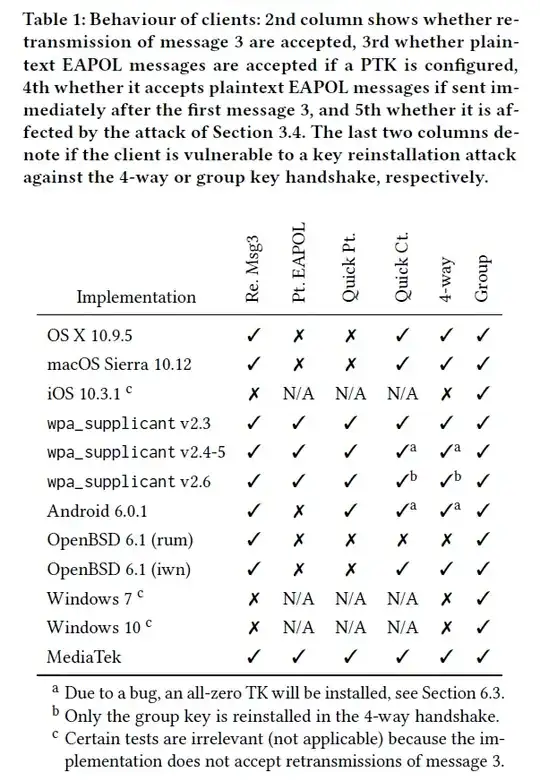
In the KRACK paper itself, the iOS 10.3.1 was marked as not vulnerable to the retransmission of the 3rd message of the 4-way handshake.
Quote from the paper:
In particular, Windows and iOS do not accept retransmissions of message 3 (see Table 1 column 2). This violates the 802.11 standard. As a result, these implementations are not vulnerable to our key reinstallation attack against the 4-way handshake.
But:
Unfortunately, from a defenders perspective, both iOS1 and Windows are still vulnerable to our attack against the group key handshake. Additionally, because both OSes support 802.11r, it is still possible to indirectly attack them by performing a key reinstallation attack against the AP during an FT handshake.
1 This is iOS 10.3.1
So both OSes are still vulnerable, but not what is "commonly" known as KRACK - which would be exploiting the 4-way handshake. I guess iOS 11.0 had a correct implementation of the 802.11 standard and this is what was now fixed. (The description in the patch notes sounds a bit fuzzy to me tbh.)
Here's a screenshot of that fancy table:
- 7,913
- 3
- 30
- 53