First of all inform/warn employees from your organization - not to click on fake flash installation pop-up windows.
Here is an example:
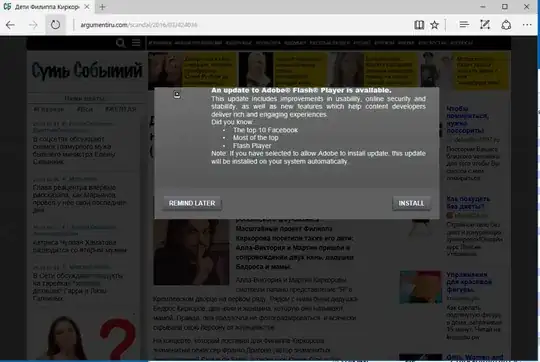
On welivesecurity.com it is said:
One of the distribution method of Bad Rabbit is via drive-by download.
Some popular websites are compromised and have JavaScript injected in
their HTML body or in one of their .js file.
That's from user perspective, now take technical advice:
- keep your software/OS up-to-date
- use strong passwords
- block traffic on SMB protocol (tcp/445)
- use AntiVirus software
- monitor scheduled tasks and service creation
And as @Royce Williams said, you can create following files:
c:\windows\infpub.dat && c:\windows\cscc.dat
and remove ALL PERMISSIONS (inheritance).
You can also block access to following compromised sites from this list - https://pastebin.com/raw/n7ExrTsJ
More info about badrabbit follow here.
