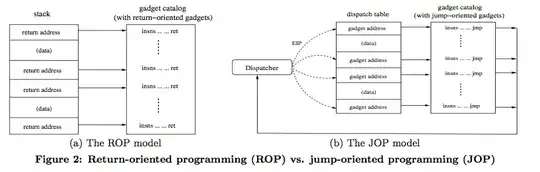
Is it possible to reliably execute arbitrary code from a single overwrite of the Global Offset Table when W^X is enabled? By "reliably" I mean assuming I control only the location pointed to by the instruction pointer and possibly some non-executable data elsewhere.
Why I ask: using the House of Force heap exploit demoed here, it is possible to overwrite arbitrary memory, which makes the GOT an attractive target for hijacking the instruction pointer. However, to make that implementation of the heap overflow work (i.e. get a shell), the author had to inject shellcode to point to from the GOT. If W^X is enabled, this technique would fail. Is there a method (possibly leveraging ROP/JOP?) that overcomes this limitation? The reason I'm having a hard time with this is because in this exploit you only control the instruction pointer, not the stack pointer, so I can't easily see a way to make ROP work, and JOP seems to require control of multiple registers to make it work (but to be honest, implementing JOP is still over my head).