I am relatively new to cybersecurity and hacking and I aim to learn ethical hacking as a passion alongside my mainstream education(Electrical Engineering).
My setup: I have set up my very own WEP WiFi network(intentionally made vulnerable by setting up WEP encryption). I have also set up a microcontroller(NodeMCU, in case you were wondering) to transmit some sensor data(DHT11's temperature and humidity data) over this WEP network. It would post the data over some URI (eg. 192.168.1.100/data).
Goal: To break into the network that the microcontroller is connected to(the WEP network) and sniff the data that is being transmitted. The communication is assumed to be by HTTP and is also assumed to happen by GET method. However, the exact URI is not known. So, GOAL 1 is to Find the exact URI and hence, get the data being transmitted. After accomplishing this, the next GOAL 2 is to try to spoof some data i.e send some garbage data and keep the actual data to ourselves.
Progress so far:
- Easily cracked the 128 bit WEP encrypted password using Kali Linux (Aircrack-ng tools). Tons of information available readily
- Got access to the gateway, i.e the modem's settings page(assuming the password is not changed from the default admin, admin User ID and password.
- Thus, obtained the IP address of the microcontroller
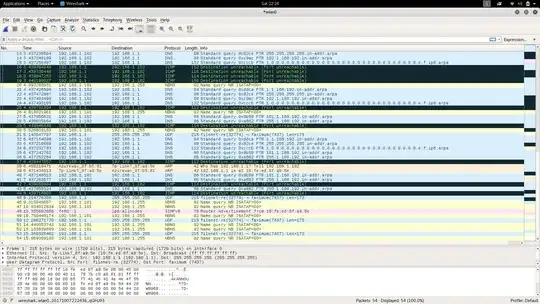
THE PROBLEM: I tried sniffing data off the network(I am still unaware of the exact URI over which the microcontroller is transmitting data). I tried using Wireshark for this. it seemed to match the needs. But, I could not see any traffic on Wireshark from the IP address of the microcontroller. No matter how many times I try refreshing the page on my mobile phone, no traffic was shown. But, however, my phone did display the data. What am I missing? I tried sniffing on the same WiFi adapter that was simultaneously connected to the WEP network. I even tried putting up an external WiFi adapter on monitor(promiscuous) mode and then try sniffing data. All in vain. I need some help.
See? No traffic is shown from the esp8266's IP address
Now, tried using an external USB adapter. This showed up the ESP as ESPressi_ac, not it's IP. The Motorola.. is my phone. When I first connect it to the network, it sends out an ARP for the IP. You can see it in the 2nd screenshot. But, it gets no response. Still, I am able to view the ESP's web page (knowing the URI beforehand).There is no HTTP traffic at all. What am I missing?