Based on the Technical White Paper
http://go.armis.com/hubfs/BlueBorne%20Technical%20White%20Paper-1.pdf?t=1505319664351
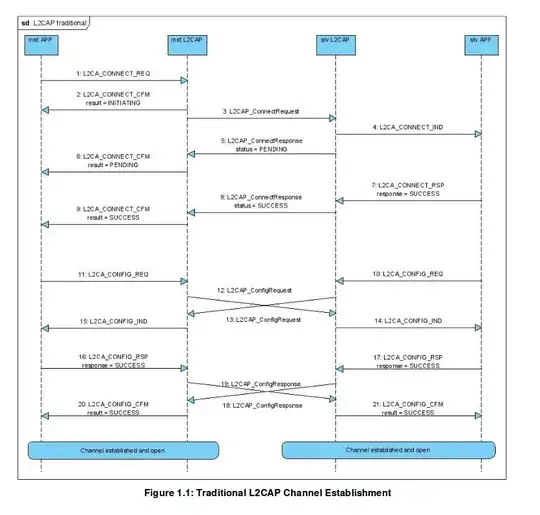
After reading it, I understand it as follows (Page 13, bottom)
So to exploit (Linux kernel RCE vulnerability - CVE-2017-1000251), there are two actors Attacker and Victim
1) Attacker sends Configuration Request with EFS element with stype set to L2CAP_SERV_NOTRAFIC
2) Attacker sends Configuration Response with result field set to L2CAP_CONF_PENDING and possibly repeated parameters for example many MTUs values, to trigger stack overflow
I am confused since, since I thought the Victim should send Configuration Response based on Configuration request from the Attacker, but in the paper it is described as above.
Is this correct? Did I misread it? Can somebody expain/correct me on this?
Thanks,
Update 1:
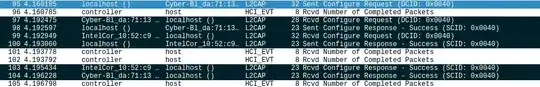
When it helps somebody, here is a Conf Request Wireshark trace.
Have these 2 adapters
Client - 00:1A:7D:DA:71:13
Server - 34:F3:9A:10:52:C9
Here with the client I set MTU to 2000
./l2cap-client 00:1A:7D:DA:71:13
mtu: ok
./l2cap-server
accepted connection from 34:F3:9A:10:52:C9
Can somebody explain this? I have TCP/IP background ....
What does it mean localhost()?
Why it sends from localhost() to Client (Conf req) than from Client to localhost() (Redvd Conf Req) than Server sends to localhost() (Recvd Conf Req) and than from localhost() to Server (Sent Conf Response) is sent and at the end Client and Server send to localhost() Recv Conf Response - Success?
Update 2:
Found this, based on this each device should send a Conf Request and each request should receive a Conf Response.
Why it looks so weird than in my Wireshark trace?
Update 3:
Ok I think, I figured it out....
Attacker
Sends:
Sent Configure Request (DCID: 0x0040)
Attacker sends Configuration Request with EFS element with stype set to L2CAP_SERV_NOTRAFIC
Receives at the same time conf request from other party:
Rcvd Configure Request (DCID: 0x0040)
Sends:
Attacker sends Configuration Response with result field set to L2CAP_CONF_PENDING and possibly repeated parameters for example many MTUs values, to trigger stack overflow
Update 4:
Going to next step ... crafting the frames, here is my next questions if anybody is interested on SO:
https://stackoverflow.com/questions/46317365/bluetooth-reply-data-frame-using-l2test