Is there a way with DMARC/SPF/DKIM to forward all emails that fail DMARC to an email address I specify?
Ie, if someone tries to spoof an email saying it's from me, and it fails, I'd like that email to be sent to an email address I specify rather than who they intended it for.
Is that something that can be done?
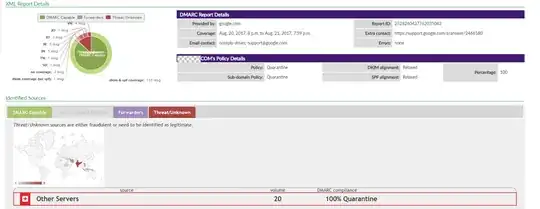
I've been running RUF/RUA for a month now, with different settings to get reports on what 3rd party services to update. However, I'm still getting some spoofing attempts from the Middle East/Asia. I'm looking to get all emails that fail DMARC to be sent to a specific email address I specify, rather than be sent to the end user(spam) or blocked.
- We use Google Apps for our Email Sever.
- All Domain information (TXT records) are stored on Route 53 on AWS.
From our RUF report I'll see an entry like this:
<record>
<row>
<source_ip>45.123.219.46</source_ip>
<count>14</count>
<policy_evaluated>
<disposition>quarantine</disposition>
<dkim>fail</dkim>
<spf>fail</spf>
</policy_evaluated>
</row>
<identifiers>
<header_from>****.com</header_from>
</identifiers>
<auth_results>
<spf>
<domain>***.com</domain>
<result>fail</result>
</spf>
</auth_results>
</record>
In this case, it would be interesting to know what was being sent out.