I don't know how to ask this because this is something new for me, I try telnet to my server and the output was like this:
Trying <IP>...
Connected to www.tjto6u0e.site.
Escape character is '^]'.
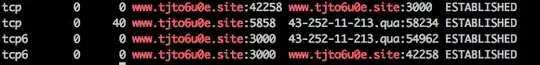
Then I tried netstat -a | grep www.tjto6u0e.site, found this:
I am using ubuntu and it was compromised before, but I have scanned my server and delete all infected files, including changing my default ssh port (22) to another one, but this one, I don't understand what is this about, is this normal or something that I should worry about?
I checked this IP 43.252.11.213 from netstat -an and redirected to a URL bulan.loket.co.id, I don't have any idea what is happening, is it meant that my site is copied to other domain?