When i use Wireshark to decrypt an Openssl sample(by importing server private RSA key) https://github.com/matthewarcus/ssl-demo it works perfect.
And i want to do the same thing with Botan CLI tools(another encryption library) using selfsigned cert and key(RSA_2048bits). I configed server using following commands
botan tls_server selfsignedCer.cer serverPrivate.pem --port=9999
client
botan tls_client localhost --port=9999
resulting
Alert:unrecognized name
Certificate validation status: Cannot establish trust
Handshake complete ,TLS v1.2 using RSA_WITH_AES_256_CBC_SHA256
Session ID : (long hex there)
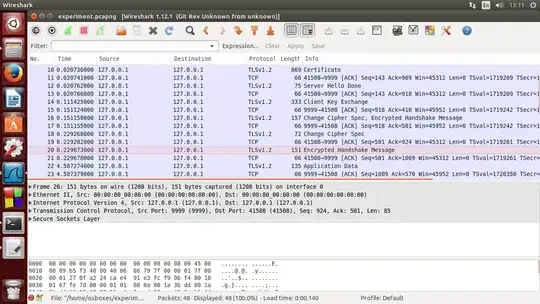
Since handshake completed, I go look into wireshark, but there is no 'SSL decrypted data' section as showed below(so it means wireshark cant decrypt that):
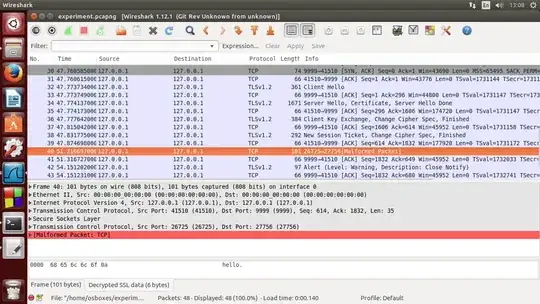
 Below is my success sample using Openssl sample , I can see the 'decrypted SSL data' section
Below is my success sample using Openssl sample , I can see the 'decrypted SSL data' section
Is wireshark only able to decrypt TLS implemented by openssl?(but I think the implementation has no effect on TLS) Or I did something wrong? Oringinal capture file and key provided below. https://drive.google.com/open?id=0B4wOLdBNMGUUQng1ak1qVFdkX0U the first 30s are the one with botan, then i stop the communication and start another openssl sample on around 40s, all using the same key