I recently read a somewhat funny article at crimeflair.net, questioning (read: murdering) the way CloudFlare provides SSL. In their words: "CloudFlare's half-baked SSL: suspicious sockets layer".
Note: The name crimeflair suggests some kind of propaganda against CloudFlare, and the text, design and images of the site almost make me feel like reading a conspiracy theory. Also the article has quite some unproven theories and assumptions. But...
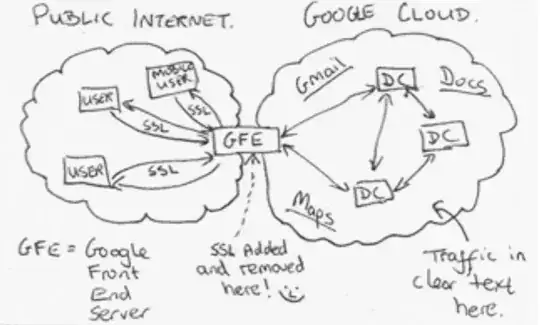
Local authorities could be sniffing the plaintext available at these data centers, and CloudFlare wouldn't have a clue.
This made me think about the current way CloudFlare works. CloudFlare is indeed a Man-in-the-Middle, encryption can never be end-to-end because then the CloudFlare CDN/proxy won't work.
Using CloudFlare's SSL to add a "free" SSL layer to some simple website of the local bakery (half-baked, got it?) seems to me like little risk. But using this in enterprise solutions with confidential data might be a thing.
It will probably protect the end-user against local network sniffing and spoofing fine! Since the connection from the end-user to CloudFlare is encrypted. But against a government or ISP that can just read the unencrypted connection behind the CloudFlare proxy towards the origin server? Probably not at all.
... it would make no difference whether the origin server has its own certificate.
Recap: CloudFlare might "secure" the availability by their great anti DDoS features but it might be a serious risk for the confidentiality and possibly even integrity of the connection due to the SSL tricks they need to use.
Interesting additional whitepaper: "When HTTPS Meets CDN: A Case of Authentication in Delegated Service" or mirror at ieee.org.
While some of those problems are operational issues only, others are rooted in the fundamental semantic conflict between the end-to-end nature of HTTPS and the man-in-the-middle nature of CDN involving multiple parties in a delegated service.
Question: Is CloudFlare's SSL half-baked since they become the Man-in-the-Middle (MitM)? And so, should it be discouraged?