Problem Description
Yesterday my mother called me that she got a message on her iPhone, that it was stolen (iCloud Find My Phone). She then had to enter security codes (two-factor authentication) into a textfield on her MacBook. I was not there at this time, so I can not really prove it. I think this was already a phishing window of the ransomware.
She is using my old MacBook, an early 2011, 13" with updated SSD and 16 GB RAM, with 10.10 installed.
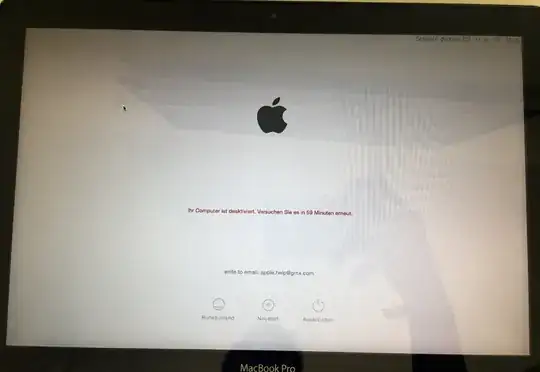
When I arrived, the MacBook was already compromised and showed following message, after booting:
The message is in german and says:
Ihr Computer ist deaktiviert. Versuchen Sie es in 59 Minuten erneut.
(Translation: Your computer is deactivated. Try it again in 59 minutes.)
write to email: apple.help@gmx.com
apple.help@gmx.com is definitely not a valid apple mail address.
I googled for the exact same message and I did not really got any good results. The only results I found were these:
How to fix it?
My thought was that it was just a screen overlay and it should be possible to boot into another OS (live Ubuntu) to get access to the data. I wanted to find a trace of the ransomware. Maybe I could find out how it is called or what it was doing with the data.
When I tried to boot to another device, the Mac was locked with a EFI firmware protection password (the same screen with the little lock was appearing). I never set this and I really doubt that my mother did it. So it could be only the ransomware.
So I first had to reset the firmware password. Luckily I found a blog entry which describes a way where you have to change the amount of RAM sticks in your system and then reset the PRAM / NVRAM. I thought it sounds a bit like magic, but on the other way, the system could not get worse.
I removed a RAM stick, booted with CTRL+ALT+P+R and waited for three reboots.
After that it the firmware lock was gone and it was possible to boot onto a USB stick. I checked for recent file changes on the mac partition, but could not find anything. The data of the home folder was not encrypted (so maybe it was a hoax).
So I made a backup of her data and then tried to do a normal boot again. Surprisingly, the ransomware message was gone! I could just boot into the system as usual.
I run a Bitdefender scan, but nothing was found. It is really mysterious and I have no idea what really happened.
Question
So my question now is, does anybody know this problem or this kind of attack? I have no clue how the attackers could set the firmware password and where the software of the ransomware was running.
Maybe it was on an own partition but I could not find it. The MacOS seems not to be corrupted.
Update
I asked an Apple Store worker today and he did not know anything about a hack like this. But he told me that it should not be possible to reset the firmware password. Only Apple is able to do that.