I recently received emails from my Origin account that my email address and security question had been changed (seems to have been someone in Russia since the new security question was in Russian). This was not my doing so I knew immediately that this was due to my account being compromised. Outside of account recovery, the only question I had left was how this happened and what to do next.
The steps I've take thus far are as follows:
- Contacted Origin support to recover my account. I did this approximately 1 hour after I was notified that changes had taken place on the account. 2 factor authentication and a new security question were applied to the account. No charges were confirmed to have taken place.
- From the machine in question, I changed passwords for other necessary online accounts. The majority of these accounts also use 2-factor authentication.
- Malewarebytes scans were performed and no exploits were found.
- From the computer in question, necessary files from my Documents folder and Downloads folder were backed up to a NAS.
- From the computer in question, necessary drivers were placed on a usb drive.
- Windows 10 was re-installed on the same disk after a format was performed using the install media from Microsoft.
My concerns are the following:
- Is it likely that whatever exploit was used to compromise my Origin account migrated silently to my NAS
- Could this exploit have migrated silently to my usb drive
- Could my password changes have been all for not since they were done from the machine in question?
- Are their any further steps I should take or any retracing of steps necessary due to what steps I've take already.
Edit: clarified #2 in that I was the one to change those passwords and not an attacker
UPDATE:
I received a curious text message today. Here is a picture of it:
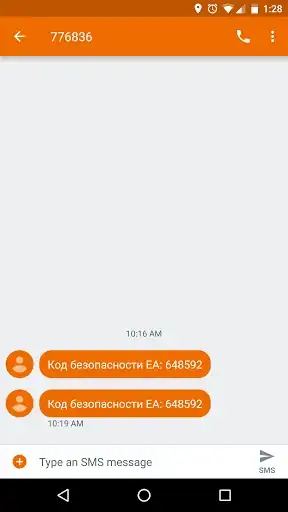
It seems 2-factor authentication has stopped whoever got their hands on my account. I would wager any service should consider 2-factor implementations at this point.