I clicked on a link (indistannews.com) and was redirected to a different website (sexiniowa.com). [Warning - the latter site is a pornography website].
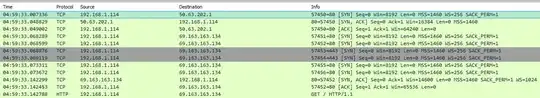
I looked at the transaction in Wireshark to try and see how I was redirected. All I see is a 3-way TCP handshake initiated by my client to the original correct IP (50.63.202.1), and then immediately after a NEW TCP handshake to a totally different IP (63.163.163.134) which contains the pornography.
Why did my client choose to drop the original connection and initiate a new connection to this second IP? What information in the first 3-way handshake (if any) prompted my client to do this?
-Nick