as one can see on the following screen photos / screenshots, I'm permanently getting ARP-spoofed:
My router's MAC adress should be "90:5C:44:E2:8D:24", as can be seen on the screenshot of my router's Web-GUI and on the sticker attached to the router (Compal ConnectBox).
However, under Windows Comodo CIS and xARP continue to warn me that I'm getting ARP-spoofed, while "arp /a" shows that 192.168.0.1 is resolved to "90:5c:44:d5:ee:65", which obviously differs after the third segment of the MAC address:
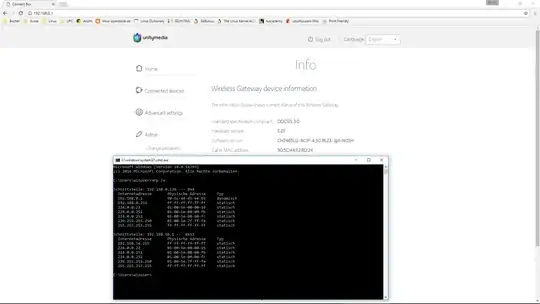
Under Linux "ip r", "arpwatch" and "tcpdump" show the same evidence for this ongoing ARP spoofing. Flushing the ARP cache or deleting a specific entry in the cache won't work, my router's real MAC address does not even appear anymore.
Normally I would assume that someone is 'branching off' the cable connection between my router/modem and the distribution box, which is located in the building I live in in order to spoof me. Even under normal circumstances doing so would be quite difficult, but I'm customer of Unitymedia, which is a German broadband company also providing internet access via Modular CMTS over their coaxial cable broadband network.
Wouldn't it require an extremely high level of technological knowledge, skill and advanced hardware to 'branch off' a modulated signal (transmitted over a coaxial cable) in order to perform ARP spoofing?
Does anyone know what performing ARP spoofing in a scenario like this would require regarding these aspects?
Maybe it would also require or could involve a manipulation of my router's firmware and/or its configuration. Therefore I uploaded the configuration to my GoogleDrive, which can be extracted and saved locally, but which has a binary format that can probably only be read by my provider (Unitymedia), unlesss someone would be able to do so. Moreover this is only the configuration, it's not possible to extract the firmware using the web interface.