I've been learning more about XSS (for the unfamiliar, Excess XSS is a great resource). I opted to get my hands dirty and give Reflected XSS a try on a local environment. I set up a very simple vulnerable PHP page running on Apache2 which takes a URL parameter and dumps the contents into the page:
<!DOCTYPE html>
<html>
<head>
<title>VULNERABLE WEBSITE</title>
</head>
<body style="background-color:#98FB98">
<h1>VULNERABLE WEBSITE</h1>
<p>Search results for <?php echo $_GET['query']; ?>:</p>
</body>
</html>
Then, I attempted to get 'malicious' JavaScript embedded into the page using a URL such as the following:
http://localhost:8082/?query=<script>alert('Hello!');</script>
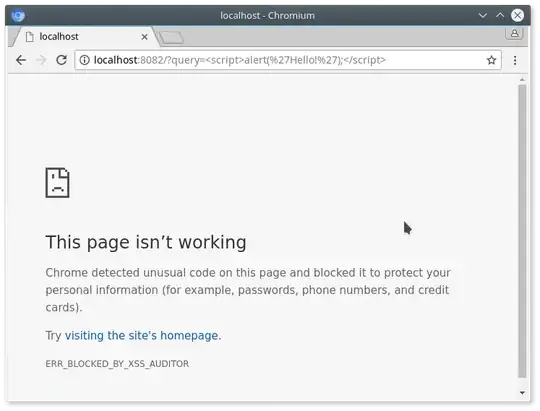
I found that the browsers themselves prevented this from happening. In Firefox, this took me to a Google Search page. In Chromium, the XSS was specifically detected and blocked:
So, going from theory to practice, I am now wondering: is Reflected XSS still a relevant security concern today?
This obviously does not apply to Persistent XSS where the malicious content is served directly by the website itself.