I was scanning an OSCP lab machine, and saw this
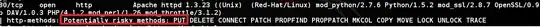
I tried to send a typical put request to test if I can put files on the server through netcat.
 However, I'm still getting a 404 error when accessing the uploaded file.
However, I'm still getting a 404 error when accessing the uploaded file.
I was scanning an OSCP lab machine, and saw this

I tried to send a typical put request to test if I can put files on the server through netcat.
 However, I'm still getting a 404 error when accessing the uploaded file.
However, I'm still getting a 404 error when accessing the uploaded file.
