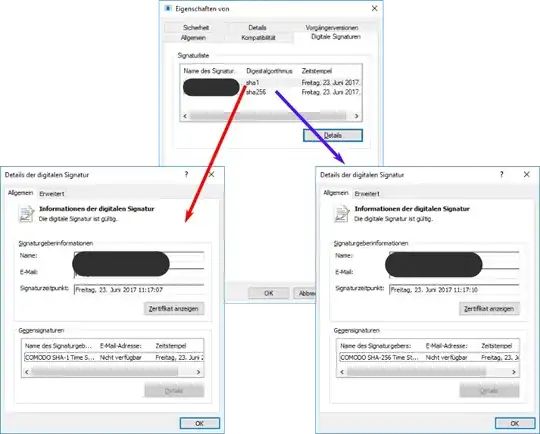
I am signing executables for our software both with a SHA-1 and a SHA-256 signature. In addition I timestamp both of these signatures.
Here I am wondering: I can timestamp the SHA-1 signature with a SHA-256 timestamp, but does that make sense? I would think that I include the SHA-1 signature only for compatibility, so I guess I should use a SHA-1 timestamp for it.
Is this correct, or should I use the SHA2-timestamp for the SHA1 signature?
The current layout looks like this: