I know it is old question but anyways here some answers since the official documentation is lacking many important details:
Documentation to AVB can be found on the Google developers site and the official code repository.
When in the Android boot process does dm-verity run?
dm-verity is a kernel extension and runs when the partitions are mounted and during runtime. However, the Android Verified Boot process starts before the kernel is loaded. To be more precise, the ROM bootloader of your device verifies the integrity of the kernel (boot.img) before loading it and therefore prevents the kernel to be corrupted. As soon as the kernel is loaded dm-verity comes into action. You should know that the implementation of the Verified Boot is customised by every vendor. For example, Huawei and Samsung use their own implementations.
Does the dm-verity run from within the "Secure World"? If so how the
"Secure World" OS loading is verified?
As mentioned dm-verity is a kernel extension and runs on kernel level and the Arm TrustZone is security extension of your CPU and runs before the kernel is loaded. The TrustZone operates on the hardware level and products like Samsung Knox use the Arm TrustZone to do real-time kernel verification. dm-verity itself does not need to run within TrustZone but it is possible that custom implementations of dm-verity use the TrustZone for cryptographic operations. For example, Samsungs uses the TrustZone for key attestation.
TrustZone is not directly part of the Android Verified Boot since it is a commercial product. It is used by companies like Samsung for additional verification of the kernel during boot phase as well as runtime. It is not necessary or mandatory for Android Verified Boot. The boot process in general with AVB can be summarised like this:
- ROM bootloader verifies signature of flashable bootloader.
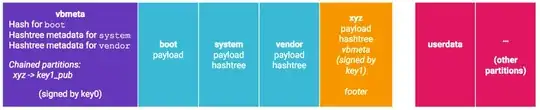
- The flashable bootloader verifies signature of vbmeta.img, boot.img and other partitions and loads the kernel. Optional: Vendor specific checks are done before the kernel is loaded or the device specific TEE OS is initialised.
- The kernel is loaded from boot.img and dm-verity checks the integrity of the partitions at mount and during the runtime of the kernel.
When in the boot process is the first time that the TrustZone "worlds"
feature is accessed/activated?
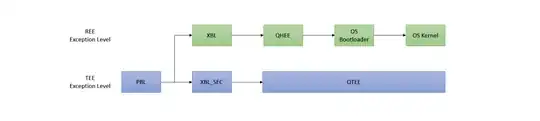
As mentioned before, according to wikipedia TrustZone is closed source and we do not know when in the boot process it is available exactly. However, usually Trusted Execution Environments are loaded before the operating system. For example, Huawei loads it's TEE after the flashable bootloader was loaded. In such cases every component just validates the integrity of the next one and builds a key-chain.