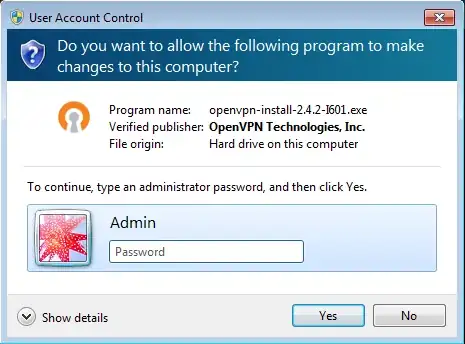
A UAC prompt appears on the secure desktop, so the normal Windows desktop (and any other open windows) are dimmed, behind a translucent black layer, with the prompt itself shown at full brightness overlaying the dimmed area. It should be centered on the main display, and contain the program name, verified publisher (in bold) and, in the case of running a file (such as an installer), the location of the file (in generic terms):
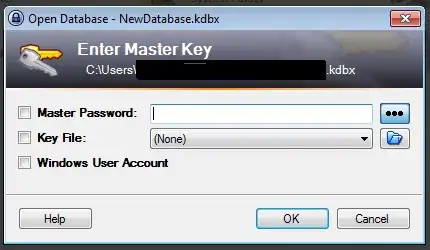
It's possible for other application to use the secure desktop to request input too. These get most of the same features: everything else dimmed, just the prompt displayed, centered:
In either case, there isn't much which couldn't be faked with a bit of effort: malware could take a screenshot of the desktop and display it in a fullscreen window with a prompt in the middle, or just rely on people not noticing that the window goes under the taskbar and show in a normal window sized to cover everything else. In terms of KeePass, they could monitor for a mouse click on a fake KeePass icon in the tray and pop up a fake prompt, then reject whatever password was entered and trigger the real KeePass executable to launch - most users are likely to assume they mistyped (especially since seeing the incorrect password display becomes a rare event after typing the master password a number of times).
If you're paying attention, they wouldn't fool you, but if you're just wanting to get your password to buy something online, they might well be good enough.

