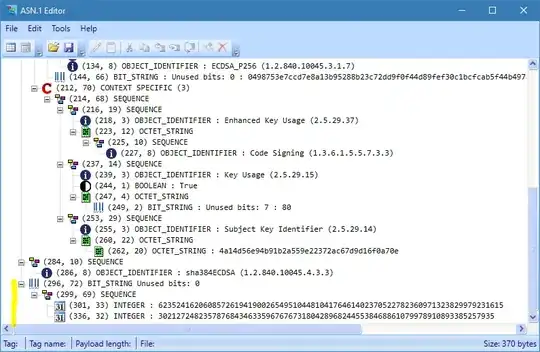
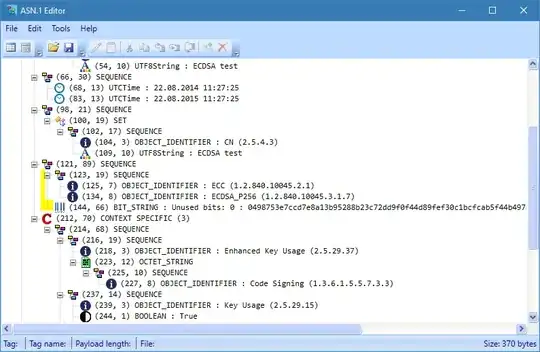
I am currently building an ASN.1 parser which supposed to decode X.509v3 certificates and epoch files in ASN.1 DER format. The parser is working well apart from one issue which I couldn't seem to get. If I decode the DER format I see that for the public key the following form of BITSTRING is used:
BIT STRING, **encapsulates** {
SEQUENCE {
INTEGER
// public key hex string
but when I look at the signature I see that it is represented with BITSTRING without the encapsulates tag and contains only the hex buffer of the signature:
SEQUENCE {
OBJECT IDENTIFIER sha256WithRSAEncryption (1 2 840 113549 1 1 11)
NULL
}
BIT STRING
// RAW signature hex buffer }
It is important for my parser to know whether the BITSTRING will only contain a buffer (like, in case of the signature) or will encapsulate some other types (like in the public key case). In the DER encoding of both I didn't find any difference that may imply usage of encapsulation.
My question being: how can I distinguish those 2 scenarios in the parser code?