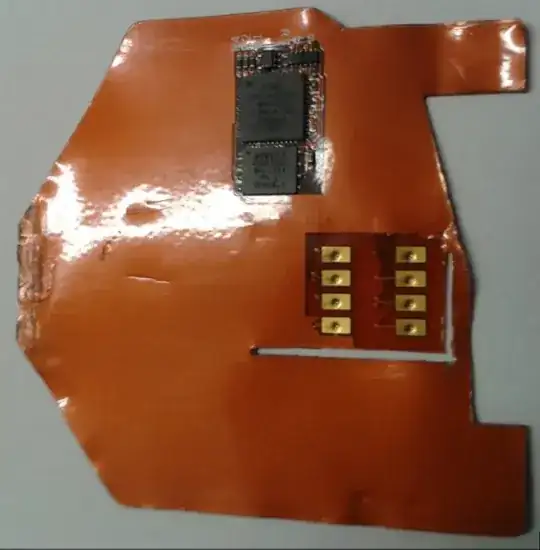
One of the verification methods supported by chip cards is "Offline with PIN", in which the PIN is transmitted to the card, potentially in plaintext. Thus, a skimmer like this can not only read the cardholder data from the chip, but it can also intercept the PIN in that particular situation.
This is enough data to encode a new magstripe card without the magstripe CCV,and for some reason some issuers do not check this CCV. Once you've captured the user's PIN you can then use this new card and the user's PIN in a terminal which does not support chip authentication and which does not check the magstripe CCV.
What's the point? With older magstripe cards the PIN is never transmitted to the card, so skimming a user's PIN requires a magstripe skimmer in addition to a hidden camera to watch users enter their PIN numbers. This actually seems like an easier way to skim PIN numbers than the previous approach.
https://krebsonsecurity.com/2017/01/atm-shimmers-target-chip-based-cards/
https://en.wikipedia.org/wiki/EMV#Vulnerabilities
Slightly more technical references: (CTRL-F for "Offline PIN")
http://www.emv-connection.com/emv-faq/
http://tsys.com/Assets/TSYS/downloads/br_faq-on-pins-and-signature-in-the-context-of-chip.pdf