The bottom line is that if an attacker can fool you into providing all the credentials, then game over. It doesn't matter about the number of factors involved. There are things which can help limit the exposure, such as very short timeouts for tokens that make it difficult for an attacker to get and reuse the token within the time limit. However, timeouts have limited protection as getting the balance right can be difficult, especially with 'fake' 2FA, which has become so prevalent and where you have to allow delays of things like SMS delivery to prevent usability problems (I have seen this using international based services where the SMS delivery can be slower and the token times out before you can receive it and enter it in the browser).
Many of the systems called 2FA are not really 2FA at all - they are actually 2SA (two step authentication). In real 2FA, the factors are something you know (password) and something you have (token, often hardware based). Schemes which involve a code sent via SMS are NOT 2FA, they are 2SA - you don't actually have the token - it is sent to you. As it is something which is sent to you, there are new threat vectors, such as having the mobile number redirected etc. This is one reason NIST has deprecated SMS based tokens as a reliable authentication process.
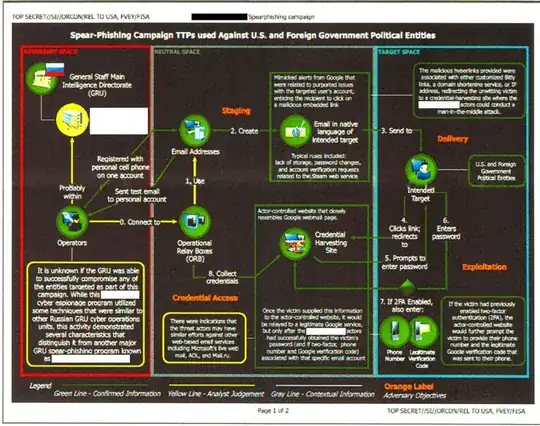
With respect to the OPs specific question, the only reliable protection is being able to detect the phishing page. Google released a chrome extension to try and assist with this. The extension will warn you if it detects you are supplying your google credentials to a page which is not a google page.
The big problem is that we have spent years teaching people to look for the "green padlock" in URLs to provide some assurance the page is legitimate. Unfortunately, efforts like Lets Encrypt have now made it easy to get domain verified certificates, so many of these phishing pages will now have the green padlock. This is not to say the problem is due to Lets Encrypt - this is a very good initiative. The problem is partly due to weaknesses in the PKI infrastructure, but mainly due to user awareness and understanding. In general, people don't understand PKI and how to verify a certificate is legitimate for the site and that the site is the site they think it is. To make it worse, even if you do understand, the steps/time it takes to perform that verification is often inconvenient or simply too hard, so people don't do it. The situation is made worse by cleaver bad actors who find ways to make things look legitimate - for example, a recent exploit uses weaknesses in how browsers display URLs and Unicode characters to generate a URL which renders in the address bar in a way that at a glance looks correct, but the actual characters in the URL specify a phishing site. The user looks at the address bar, sees a green padlock and glances at the URL which looks right (your brain will even fill things in to make the match look better!) and accepts the page as legitimate. You don't notice some additional whitespace between characters or slightly odd looking character shapes.
So how do we protect against this. Unfortunately, there is no single "do this and you will be safe". Some password managers can help as they will only provide the credentials if the URL is correct, never use URLs in email messages - always type it in yourself or use a bookmark you created. assume at some point you will be fooled and adopt practices which will limit the damage when it occurs i.e. different passwords for every site, use hardware based 2FA when possible, actually click on the certificate details button for "high value" sites and look at what it says and who the certificate is registered to, make sure your system has all updates and your using the most recent browser version etc., be suspicious by nature and remember that the big threat is social engineering, so be very wary about anything which pressures you to take action based on fear, guilt, rewards or punishment. These are very effective motivators and threat actors rely on them. Phishing campaigns have become much more sophisticated in their implementation, but at their core, they still rely on emotional manipulation - a promise of something wonderful or a threat of something terrible.
Finally, if you’re tempted to comment because of my mention of password managers, please don't. Yes, there are risks with password managers and yes, some are worse than others. However, in general, a good password manager used correctly is usually going to provide more protection for the average user than their current password management process. Yes, if the password manager gets compromised, then all of your passwords are compromised. However, many people find password management too hard and are using the same, often weak, password on every site anyway. Once one site is compromised, all their sites are compromised. Obviously, if you understand technology and you understand passwords, hashing etc., you can probably come up with a more secure solution, but you’re not the audience for password managers. Think about how your parents or grandparents are dealing with password management and how well they spot phishing sites or understand certificates and then think about how easily they can handle your custom GPG based password management over cfile or synching.
EDIT: On re-reading my response, I'm not sure I emphasised enough that real 2FA is increasingly available and many of the providers who currently support the less secure 2SA with SMS codes also support far more secure 2FA, in many cases using U2F (as mentioned in other replies). Hardware 'keys' from Yubico or duo (and others) are cheap and easy to setup/use. My only recommendation is that if you decide to go the hardware token/key route, make sure you get two keys, register them both and put one key away in a secure location. I have one which I carry with me and one which I have in a safe at home. Recovering from a lost/damaged key is not as easy as recovering from a forgotten password, so you want to avoid getting into that situation as far as possible.