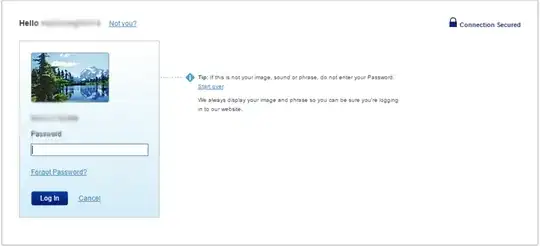
Well, I only have two examples, but it seems to be a slowly growing thing.
First, I noticed that hotmail.com/live.com started to do this - ask for the email address on the first screen, and then you have to click 'next' and then enter your password.
... Man, is this annoying! At least trusty gmail knows good UX. A few months later gmail are doing the same thing.
So, I assume there is a security reason for this workflow because it can't be for UX (?)
But what is the reason? Is it to do with tricking bots/making their life more difficult?