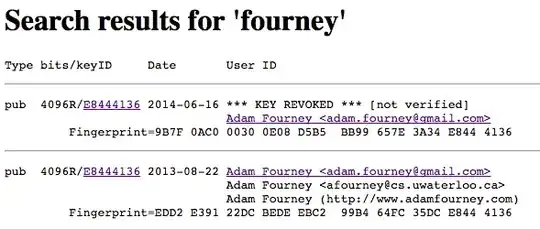
I recently noticed that someone has created an elaborate forgery of my OpenPGP key. Specifically, they orchestrated a short key (32-bit) fingerprint collision, and also forged additional keys to match those that signed my original identity (also orchestrating short fingerprint collisions):
(http://keys.gnupg.net:11371/pks/lookup?search=fourney&fingerprint=on&op=index)
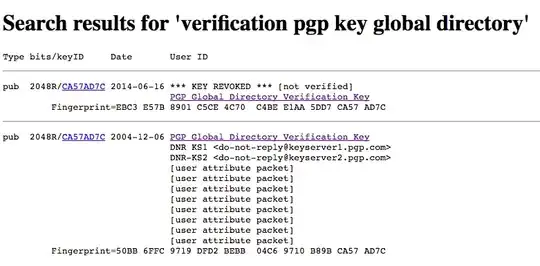
Worryingly, this includes creating a forgery of the PGP Global Directory Verification Key,
(http://keys.gnupg.net:11371/pks/lookup?search=PGP+Global+Directory+Verification+Key&fingerprint=on&op=index)
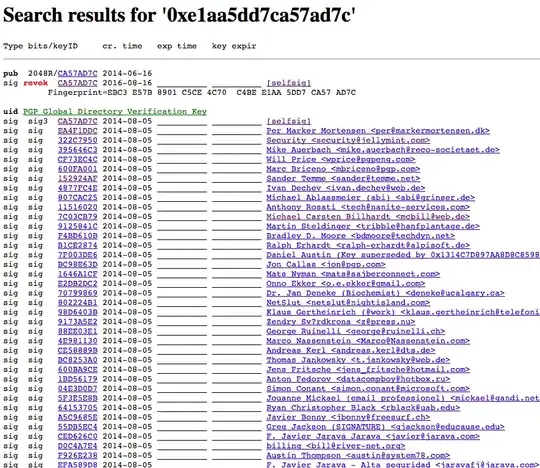
together with a huge network of forged keys that sign its identity -- again, exploiting 32-bit fingerprint collisions:
(http://keys.gnupg.net:11371/pks/lookup?op=vindex&fingerprint=on&search=0xE1AA5DD7CA57AD7C)
This was a huge amount of work. Given that all these keys are revoked, I suspect this is the work of a security researcher who is out to prove a point.
However, given that GnuPG and these keys servers rely heavily on short fingerprints, I think this effectively breaks the entire public key server system.
My question is therefore twofold:
- What can be done to combat this problem, or reverse the damage?
- Can the public key server system still be trusted?