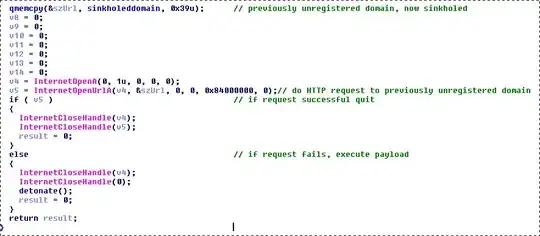
I read the Article of WannaCry on malwaretech.com and as far I understand it works like this:
- Try to connect via HTTP to www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- if it got an response then exit.
- if not, do the next part (encryption etc.)
As far as I know, did the register of an unregistered domain make the (first) WannaCry not operable anymore?
The reason this was that a part of the code checks if it got an answer when it opened a network connection to that domain.
So if the Request that would be sent to the (theoretical) not existing Domain and the Proxy will, instead of just try to connect and got an "Connection Refused" message, redirect the Traffic to an existing host (which mostly just say that the URL is not reachable), would the (first) WannaCry never go active?