Based on answers to the question How is the “WannaCry” Malware spreading (...), I understand it leverages vulnerabilities present in the SMB implementation. Assuming an unpatched and otherwise vulnerable system, would EMET (properly set-up to enforce DEP, SEHOP, ASLR and certificate pinning, in addition to importing the "Recommended Software" and "Popular software" mitigation lists) prevent this exploitation?
2 Answers
No, EMET won't prevent exploitation.
WannaCry uses the ETERNALBLUE exploit, targeting the MS17-010 vulnerability. This vulnerability exploits the Windows File Sharing Service (a.k.a SMB) on TCP port 445. This Windows File Sharing Service runs with SYSTEM level privileges, under the SYSTEM process - basically at the kernel level.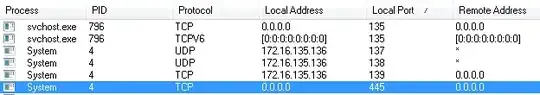
On the other hand EMET is a user-space protection tool to protect user-space processes like browsers, browser plugins or Office applications. EMET is injecting a DLL into every protected application, and provides protection through that DLL. By default, EMET provides almost no protection to the system (except enforced DEP, enforced ASLR, SEHOP). It only protects applications (Executable files) which have been configured to be protected by EMET.
A logical step would be to configure EMET to protect the SYSTEM process, but unfortunately this is not how operating systems work. Different memory protection strategies and implementations are needed to protect user-space processes and the OS kernel.
- 611
- 3
- 12
-
1Good answer, but I wonder exactly how does it exploit the SMB Service? From what I read [(here)](https://security.stackexchange.com/a/159663/91904) it's a buffer overflow exploit, which I would think should be mitigated by enforcing DEP for all processes. – Marc.2377 May 17 '17 at 20:17
-
@Marc.2377 DEP (NX) protects from trivial buffer overflows, but there are numerous ways to get around that protection with that primitive. – forest May 03 '19 at 23:51
EMET is a set of tools. It won't do anything by itself.
If properly used, you can counter malware with it, but you can do the same with a properly designed .bat file.
So the answer is no, not by just having it installed.
- 8,779
- 3
- 19
- 28