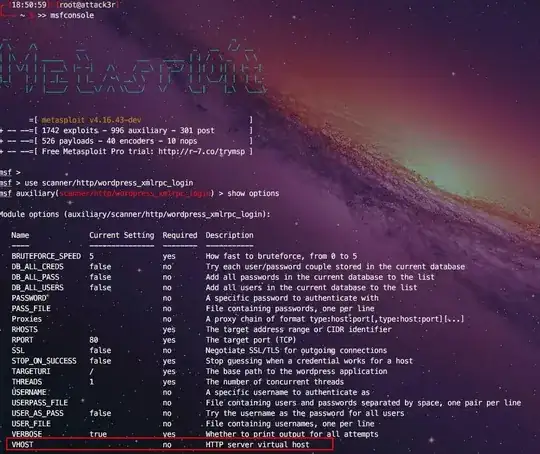
There is a website which I want to audit. That site must have a concrete Virtualhost configuration because if you access to it using the domain name the website is shown, but if you use the ip address the website is not shown.
If I launch an exploit using Metasploit against a site with this kind of configuration, it doesn't work. I think is because Metasploit is replacing the domain name by the resolved ip address and in that way the website is not responding as expected.
Example:
Take an apache serving a Wordpress site (htttp://example.com) with that kind of Virtualhost explained configuration. This site has the XMLRPC api enabled. If I use a tool like wpscan for example, you can put the url of the site (using --url htttp://example.com) and it works. But if I try to use the auxiliary/scanner/http/wordpress_xmlrpc_login Metasploit module, after setting the RHOSTS var with the domain name (set RHOSTS example.com) and launching the exploit, the module is answering:
[*] x.x.x.x:80 :/xmlrpc.php - Sending Hello...
[-] XMLRPC is not enabled! Aborting
In the response there is the ip address and not the domain name. So I guess is because as I explained, Metasploit is resolving and changing RHOSTS var with the ip address value and then the module is failing because of the web server Virtualhost configuration.
So the question is:
- Is there a way (maybe a plugin I don't know) in Metasploit to avoid this transformation/replacing?