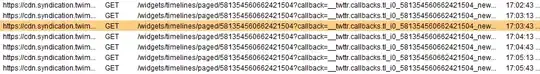
While trying to work on incident investigation, I am seeing continuous https requests from website
cdn.syndication.twimg.com:443/widgets/timelines/paged/
callback=__twttr.callbacks.tl
domain=www.kali.org
These requests are continuous and are tagged as something (file with PDF/Xls or similar extension) is getting uploaded from the host PC. The user computer is a Developer[DVPC] and I don't want to intefere if he is using this appliaction as legit, however with continuous https requests every 10 minutes and that too from kali.org[while we are windows based environment], it bothers me what the user is trying to achieve here. Can someone assist me with this?
I understand my question is a bit unclear, however I am trying to understand if it should be termed as legit or this website be blocked on the proxy?