This is a repost, because i accidentialy posted on stackoverflow first
I was wondering how i could achieve a high security level, using Client-Server Authentication. Below is a rough draft of what i thought about:
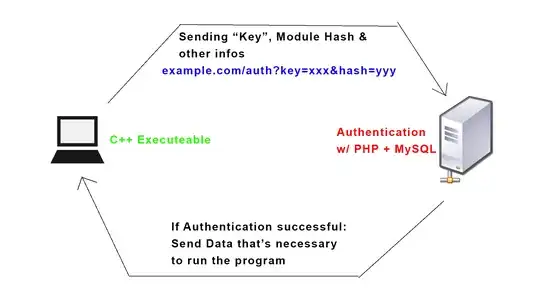
Let me explain it a bit more:
- The C++ executeable is running on a gaming console which has an unique ID the user uses to sign up on my website
- When the executeable is launched it will get the current module/file hash of the executeable and the unique ID ("Key" in the sketch) and do a webrequest to my website (example in blue on the sketch)
- The auth.php on my website will then check if the file hash is the same as the file that was given out (detecting if the file was modified). It will also check if the "Key" is connected to a user
- Then it will send back individual info from that user and also some data/offsets needed for the executeable to run properly later (This would prevent the attacker theoretically from just noping the internet connection, so he has to make a call to my website to get data that's needed to run the executeable properly)
Sounded good to me at the beginning but then i noticed some flaws:
- Even though i'm obfuscating and encrypting the file a hacker will still be able to disassemble it. That mean's he could take out my check if the key is spoofed and just send the key of a registered user (he can also edit the hash that's sended to prevent the whole check if the file was modifed what makes it kind of redundant)
- He could also read the data that's sended after a successful auth and then nop the internet connection, so there's no call to my website anymore and insert the data he got into the executeable to make it work
No matter of the security on the executeable a hacker will always be able to disassemble/decompile it at some point. That's why i think the Client-Server Authentication has to be so that even if the client is hijacked it won't be able to authenticate. I don't really know if that's even possible or if it's just the wrong approach.
I would really appreciate if you could leave some thoughts or ideas down below. Thanks for your time and have a good day :)