Why does openssl show different certificate chain for mail.google.com:443 than what Chrome/Firefox shows?
$ openssl s_client -connect mail.google.com:443 < /dev/null | head -10
depth=2 /C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
verify error:num=20:unable to get local issuer certificate
verify return:0
DONE
CONNECTED(00000003)
---
Certificate chain
0 s:/C=US/ST=California/L=Mountain View/O=Google Inc/CN=mail.google.com
i:/C=US/O=Google Inc/CN=Google Internet Authority G2
1 s:/C=US/O=Google Inc/CN=Google Internet Authority G2
i:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
2 s:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
i:/C=US/O=Equifax/OU=Equifax Secure Certificate Authority
---
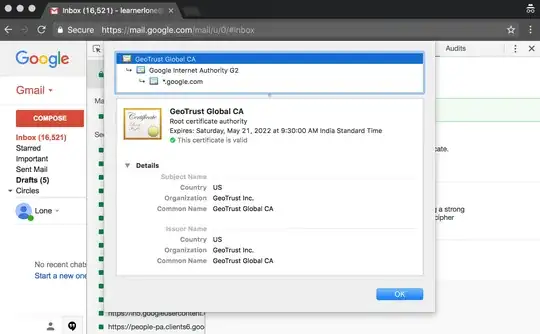
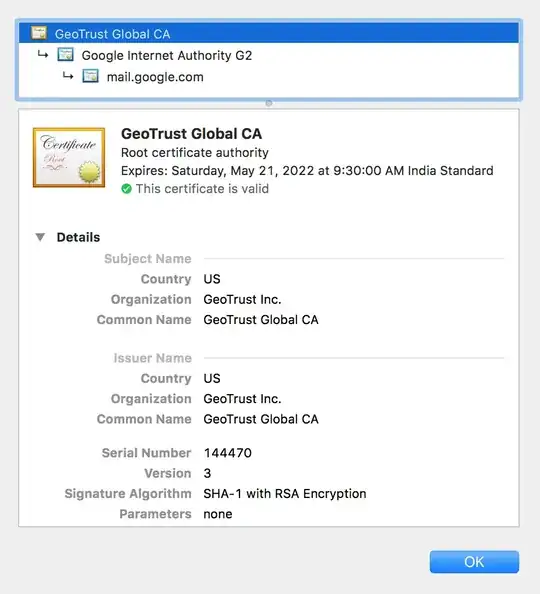
The above output shows that the top-level certificate belongs to GeoTrust Global CA and it is issued by Equifax Secure Certificate Authority. The server certificate is issued to mail.google.com.
But Chrome and Firefox shows that the top-level certificate is a self-signed root certificate by GeoTrust Global CA. The server certificate appears to be issued to *.google.com.
Even after disabling QUIC via chrome://flags, I still can't see the Equifax certificate in the certificate chain, although the server certificate now appears to be issued to mail.google.com.
Why do I see different Equifax certificate in OpenSSL but not in Firefox/Chrome?