Handshakes are different for WEP networks. The handshake you expect to capture is the "four way handshake" and that is only existing on WPA and WPA2 networks.
On WEP networks the handshake is different, is a challenge response handshake. This is how it works on WEP networks:
In Open System authentication, the WLAN client need not provide its credentials to the Access Point during authentication. Any client can authenticate with the Access Point and then attempt to associate. In effect, no authentication occurs. Subsequently, WEP keys can be used for encrypting data frames. At this point, the client must have the correct keys.
In Shared Key authentication, the WEP key is used for authentication in a four-step challenge-response handshake:
The client sends an authentication request to the Access Point.
The Access Point replies with a clear-text challenge.
The client encrypts the challenge-text using the configured WEP key and sends it back in another authentication request.
The Access Point decrypts the response. If this matches the challenge text, the Access Point sends back a positive reply.
On WPA/WPA2 networks is working in a different way. Look at this:
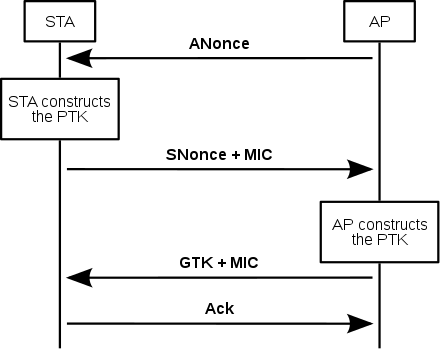
Extracted from here. On that link there are a lot of more info about it.
To crack a WPA/WPA2 key you need to capture the 4 way handshake, but for WEP is not needed. The WEP algorithm is bad designed and with enough captured traffic you can get the key. There are a lot of tools which can manage all of this (capturing WPA/WPA2, WEP decrypting, etc). I'll recommend to you this complete tool: airgeddon.
Hope it helps.
