For context I recently started working through the WebGoat appsec training program, and have hit a wall passing data to a program needed to complete a lesson.
One of the first lesson sets is entitled ""Access Control Flaws".
The first lesson description states:
The 'guest' user has access to all the files in the lessonPlans/en directory. Try to break the access control mechanism and access a resource that is not in the listed directory. After selecting a file to view, WebGoat will report if access to the file was granted. An interesting file to try and obtain might be a file like WEB-INF/spring-security.xml. Remember that file paths will be different depending on how WebGoat is started.
Current Directory is: /.extract/webapps/WebGoat/plugin_extracted/plugin/SqlNumericInjection/lessonPlans/en
Choose the file to view: (List of files is below)
Choosing a file from the list gives an error that it is in the list. At first I tried manually typing out URLs, but realized I'd have to modify the request somehow. I caved and looked at the solution, which states:
This lesson can be solved by intercepting the filename in WebScarab and replacing it with ../main.jsp which is a file located in a folder below the current directory.
Ok, so my instinct was correct - now comes operationalizing my intention into action.
Googling found that WebScarab == the old name for the OWASP Zed Attack Proxy.
More Googling found that in order to pass data to ZED, I needed to set up a proxy in Firefox.
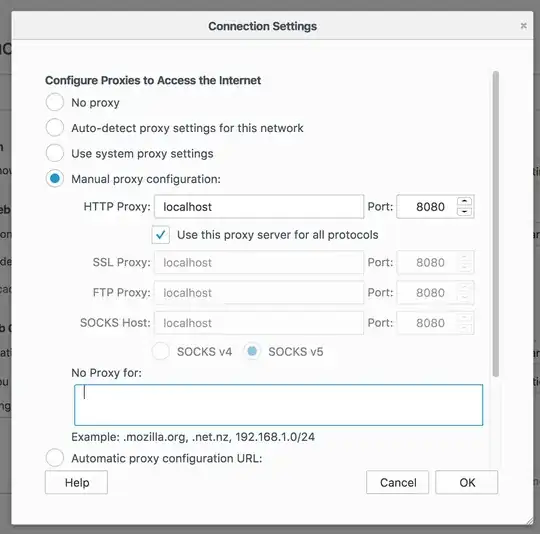
So I went into Firefox, and set up the proxy. Note that 127.0.0.1 and localhost have been removed from the "No proxy for" field, :
However, when I navigate back into WebGoat (which is hosted locally at localhost:8080/WebGoat), nothing is intercepted. Traffic to external websites is is intercepted, so I suspect the issue is that for some reason ZAP is not receiving my WebGoat traffic.
I'm sorry this is a bit of a simple question, but I've researched a lot and can't seem to find any solutions.
TL;DR: How can I make sure ZED intercepts localhost traffic when viewing OWASP GOAT lessons in Firefox? (Traffic to external websites is intercepted, just not localhost traffic)