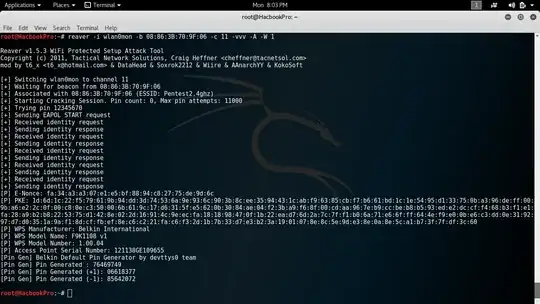
I've been conducting some simple penetration tests on a few older wireless routers that I have lying around, focusing mainly on WPS vulnerabilities. I've been having some trouble with an old Belkin router (model F9K1108v1). The router doesn't seem to be vulnerable to a Pixie Dust attack. However, I was able to acquire the router's WPS PIN using the generate PIN option in reaver.
I have access to the router configuration and I can verify the PIN that I acquired is correct. This is an unusual attack situation for me, as I am not used to acquiring only the router PIN. I can't seem to make any further progress with the PIN. I attempted to acquire the router's WPA key using multiple options in reaver, such as mimic windows 7 registrar, to no avail. I also took similar steps using bully, but still made no progress.
What are some logical next steps after having successfully acquired only a router's WPS PIN?