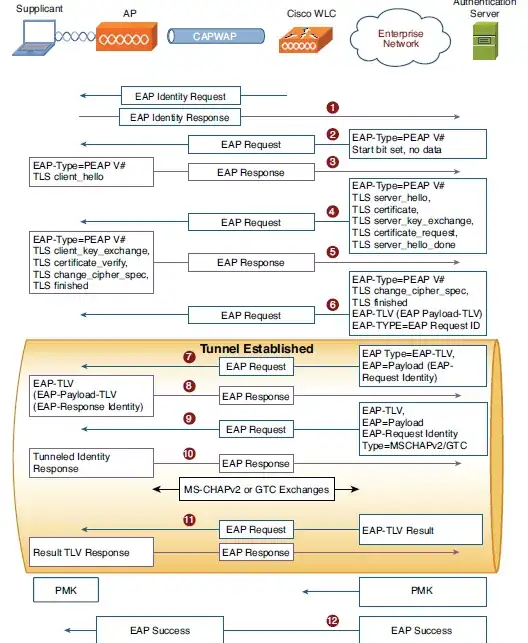
From my understanding, after the Access-Request, the authentication server (RADIUS) sends a reply (encapsulated in the Access-Challenge packet) to the authenticator (AP).
The Access-Challenge packet contains an EAP Request in which it is specified the EAP method that the supplicant should use.
The supplicant can then acknowledge that EAP method or NAK it and replying with another EAP method that can be used.
My questions are:
1) In the EAP Request are both the EAP method and inner authentication specified?
2) Is it possible for the administrator of the RADIUS to specify a default EAP method and inner authentication, such that the EAP Request would contain always the chosen method?
3) It is possible, by using scapy, to edit the EAP Request and specify another EAP method and inner authentication?