Let's start with the cynical view:
Certificate Authorities are for-profit companies, so they will charge as much as they are able to get away with!
More seriously, running a certificate authority is an expensive, low profit margin business, but the answer really comes down to the type of certificate you want.
Domain-Validated (DV) Certificates
For a basic DV cert which, makes your browser address bar look like this:
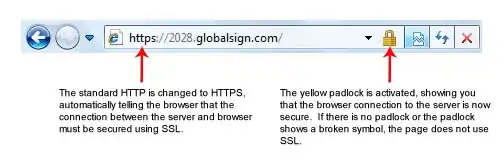
the costs are very low - basically the CA just needs to confirm that the person requesting the cert had control of the server at the time of request. This can be fully automated. As @SteffenUllrich points out, in 2014 the Electronic Frontier Foundation, Mozilla, and the University of Michigan teamed up to set up a 100% free CA Let's Encrypt for issueing DV certs. Based on the use-case you described in the question, it sounds like that would suit your needs.
Extended Validation (EV) Certificates
If you want the high-end certs that include your verified company name and country in which it is registered to appear in the browser like this:
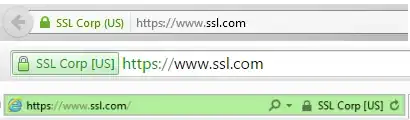
then there is significantly more cost to the CA. Before issuing an EV cert, the CA is required to have a human verify a whole pile of things about the legal status of your company. Things like: is your company legally registered under the name listed in the cert request? Is the person requesting the cert listed as a legal officer of the company in the company's registration documents? Is the DNS record for the requested website registered to the same company? etc.
Why a recurring fee?
The reason that CAs charge a recurring fee is the same reason that you can't get a 10 year SSL cert: the CA/Browser forum requires certs to expire and be completely re-validated every year or two. The security reasons for this are to force key rollover, to prevent the company from going bankrupt or changing name and a rogue sysadmin from continuing to use the cert nefariously, etc.
The CA is required to do all this background checking not only on first time issuance, but also every time the cert is renewed. The added value for you is that your customers get a higher level of assurance in the trust-worthiness of your website (sure, 99% of consumers won't notice, but auditors and hackers certainly will!), and also, Google is moving towards giving higher search preference to sites with higher quality certs.
This is why certs can cost hundreds of dollars per year; you are not just paying for a couple bits of data, you are paying for the time of the human who has to do the verification.
OCSP servers
There are also server costs for maintaining a cert, mainly the costs of OCSP, which requires the CA to maintain high-bandwidth, low-latency, zero-downtime servers for responding to revocation checks on each cert they issued. While this might not sound expensive, every web browser must ping a CA's OCSP server during every HTTPS page load. Every extra millisecond that the CA takes to respond adds to the page load time of every page on the internet. Running a low-latency server at this level of traffic is a tricky network engineering problem.
[disclosure: I work for a CA]

