To effectively communicate with business owners or executives on security, specifically with how people may harm their business, it often helps to discuss what types of people worry them. What are few good lists to kick-off such conversations?
6 Answers
Loss of revenue is the only threat you really need to talk about with business people. Frame the issue in terms of money and emphasize that money will be lost if security is not given a high priority. Explain that money can be lost in the following ways:
- Lawsuits due to disclosing sensitive user information.
- Bad publicity, which damages the brand, which, in turn, results in revenue loss.
- Unsecured checkout processes open up the avenue for lawsuits and also reduce sales.
- A non-functioning website reflects poorly on the business, hurts conversions, and reduces traffic over time.
It is better to have a risk-management approach to security to minimize the possibility of these risks occurring. In the end, it will cost less to be proactive than to be reactive.
- 3,142
- 3
- 26
- 32
-
It should be noted that in certain phases of the business, loss of revenue isn't so much a concern....especially if you still have little or none. Getting the product launched can still be a much higher priority. – Eric Falsken May 15 '11 at 09:22
-
1Future revenue is still a consideration. Any of the points above could kill a business before the product even starts making money. – VirtuosiMedia May 15 '11 at 22:05
As @VirtuosiMedia says, protecting revenue is the "killer feature" for IT security. You can couch questions about threats in terms of costs:
- what would it cost to replace that server if it were stolen?
- what about the cost to replace the data on the server?
- what would be the opportunity cost in lost business during the recovery period?
- what would it cost the business if someone else used the stolen data?
...etc.
-
And dont forget the "soft costs" such as reputation (for those that care...) – AviD Dec 08 '10 at 12:25
-
@AviD: indeed. Easiest way to make that relevant: "what would be the results of a lawsuit brought against the company by a customer whose data had been stolen?" – Dec 09 '10 at 12:21
-
1Yeah, that works. Or "... of a front page article in the New York Times about a horrendous security breach in your systems" – AviD Dec 09 '10 at 12:23
One of my favorite lists for kicking of such conversations was created by Intel IT Security.
It can actually be fun to run down the left hand column ("Agent Label") and discuss which type of people are most likely to harm your business. Then the game is to decide what to do to minimize their chances of success.
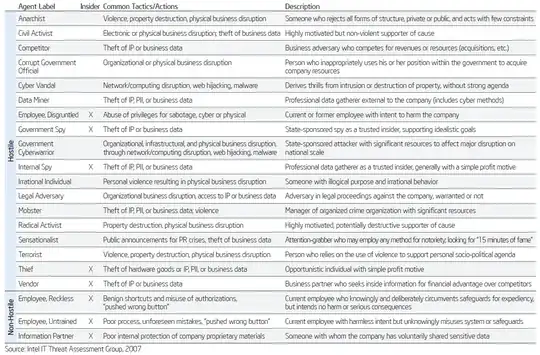
You can download the PDF to gain more detail: http://www.intel.com/it/pdf/threat-agent-library.pdf
- 13,714
- 3
- 40
- 83
-
2I don't like this because it doesn't convey the power of collusion or conspiracy. The underground community and underground economy puts all of these guys in the same room together and gives them tools to trade. – atdre Nov 14 '10 at 14:24
-
1Excellent point. Nearly all of the businesses I do work with are within the bottom range on the scale of security maturity and they have never pondered threat-centric security, much less targeted attacks by communities. I like the idea of extending the chart above with your observations. – Tate Hansen Nov 14 '10 at 17:37
-
To be fair this list seems quite subjective and arbitrary, and not very useful in practice. I (and you too) can come up with as many fancy names as we want to try to characterize the behavior of "agents" but what's the point? – Andreas Bonini Sep 26 '11 at 00:35
-
Personally, I'd start with getting the representatives of the business talking about their most valued assets. People who are not security professionals generally have a very hard time figuring out threats. And an even harder time figuring out what threats should matter most to them. But most good business people knows what's important to their business - the repuation, their products, their revenue streams, keeping costs low. And people love to talk about what matters to them. Get them engaged first.
Then take the the threat analysis angle through risks to those valued things. If if this is the preliminary discussion, you won't know what vulnerabilities can be exploited yet - but going through threats in light of harm to assets makes it real.
As far as lists, I'd have in my back pocket lists of threats for common asset types. For example:
- reputation - threats include competitors launching malicious attacks, employee mistakes, professional hackers looking to make a name for themselves,
- revenue - theives looking to put revenue in their back pocket (can be inside as well as outside the company), damage from lawsuits that come from incorrect protection of personal data, damage from fines from regularatory govt. bodies, etc.
I'd be prepared to tailor each list to suit the client. If you aren't actively tailoring the list to address the audience, you'll give the impression that security is a rote procedure.
- 11,606
- 1
- 27
- 58
I typically give two examples of loss of revenue, downtime and fines from opposite ends of the scale - Worldpay's $9M loss in 12 hours from a very simple exploit, and a local small business - to make sure the audience don't feel it couldn't happen to them.
- 61,367
- 12
- 115
- 320
The attacks Anonymous aim at large companies is starting to be a great conversation starter. It used to only get interest from organisations with an interest in IP, DRM, music rights etc., but these days Anonymous are in the media enough with a wide enough range of targets that the conversation has wide appeal.
It also lends itself well to not only IT security based discussion, but also topics including risk, disaster recovery and business continuity, secure data management etc.
- 61,367
- 12
- 115
- 320