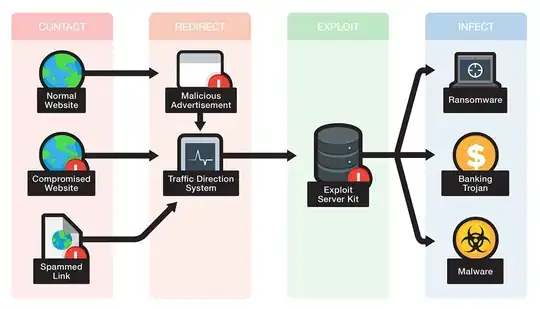
was for someone on the inside to click, or type (or otherwise GET / HTTP/1.1), and access his public URI.
Is this realistic? Surely whatever exploit and payload was used, must require more manual execution than that, right?
There is a phrasing ambiguity in this. "Is a GET enough"? -- no, of course. But is clicking a link, with a vulnerable browser, enough? It is.
It is not the act of GETting a payload that infects the system per se, the problem lies in what is used to do the GETting. That is why you want defense in depth:
- proxy "guard" software to stop navigation to unsafe shores (the GET never starts),
- firewall/antivirus to recognize the payload and possibly prevent it from calling home and downloading a bigger brother (the GET does not succeed),
- continuous system update to ensure vulnerabilities are kept to a minimum (the GET succeeds but has no effects),
- IDS to detect suspicious behaviour inside the network (the effects are detected and blocked)
- backups.
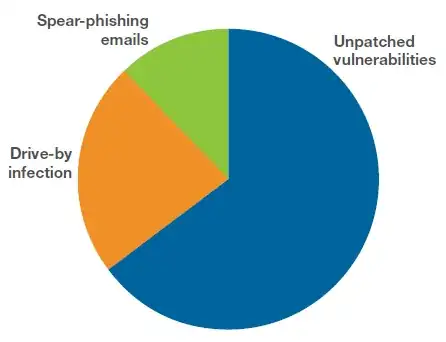
If the system is not updated and a browser is vulnerable, the targeted URL might recognize the browser and send a tailored payload (which it wouldn't send to, say, a content-detection system or a site scanning service, in order to appear clean). If the vulnerability allows it, the downloaded content might be able to run itself and take control, and possibly download further, less specific malicious code.